2023.09.12
| CVE-2021-39805 | A-212694559 | ID | High | 12, 12L |
|---|
patch
分析
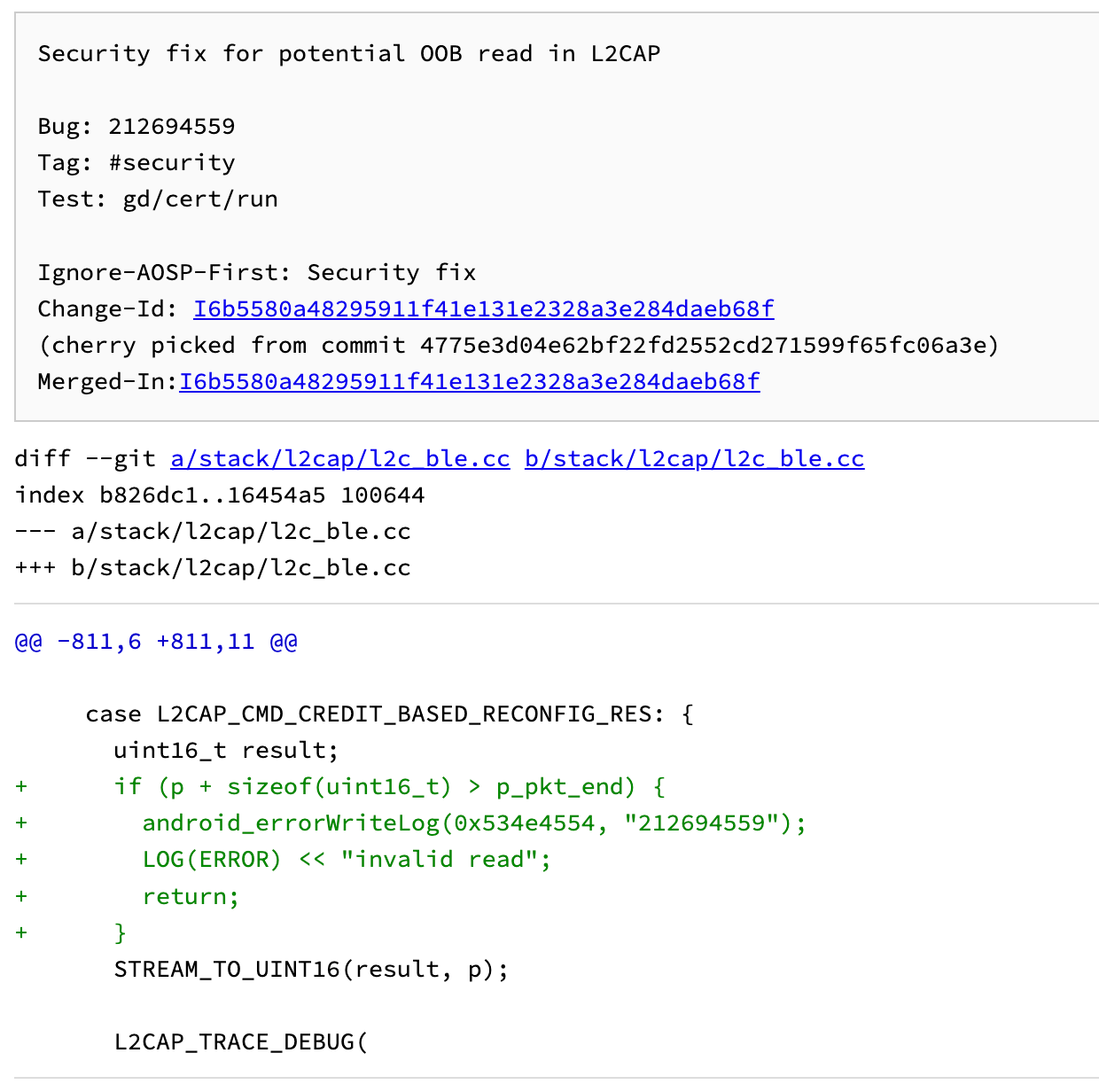
该漏洞发生在L2CAP的Enhanced Credit Based Flow Control Mode(基于信用值的高级流控模式)的实现中。
漏洞根因很明显,STREAM_TO_UINT16(result, p);从 packet 里读取数据给result之前,没有判断这个packet是否还有数据。
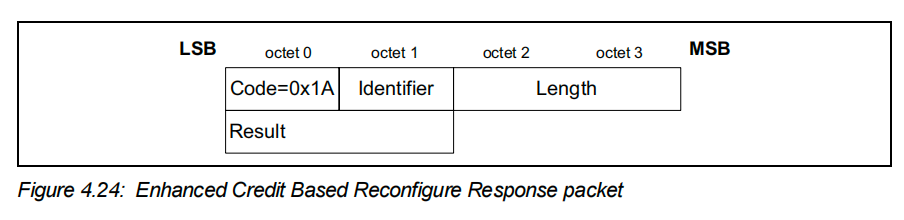
看下面第三个图,若攻击者构造的信令packet里的command只有前三个字段,即Length = 0,也就是没有Result字段时,代码中【1】处就会发生OOB Read。
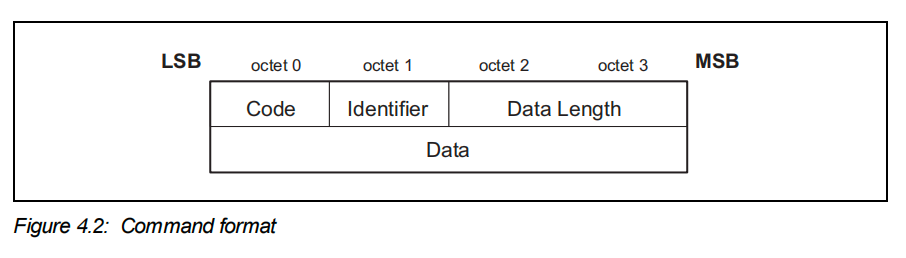
- 信令packet中command的格式
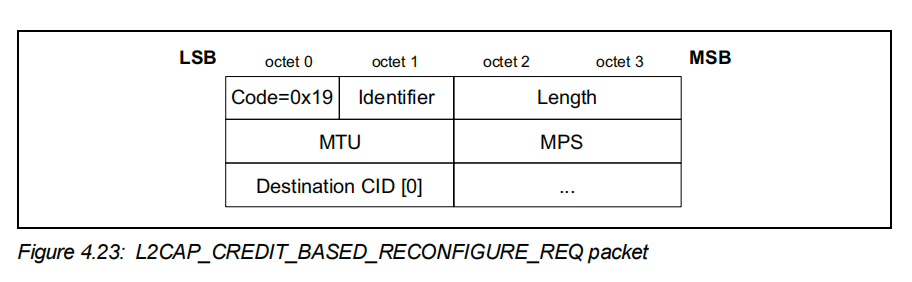
- credit相关的两种command的格式
/*******************************************************************************
*
* Function l2cble_process_sig_cmd
*
* Description This function is called when a signalling packet is received
* on the BLE signalling CID
*
* Returns void
*
******************************************************************************/
void l2cble_process_sig_cmd(tL2C_LCB* p_lcb, uint8_t* p, uint16_t pkt_len) {
......
STREAM_TO_UINT8(cmd_code, p);
STREAM_TO_UINT8(id, p);
STREAM_TO_UINT16(cmd_len, p);
/* Check command length does not exceed packet length */
if ((p + cmd_len) > p_pkt_end) {
L2CAP_TRACE_WARNING(
"L2CAP - LE - format error, pkt_len: %d cmd_len: %d code: %d",
pkt_len, cmd_len, cmd_code);
return;
}
switch (cmd_code) {
case L2CAP_CMD_CREDIT_BASED_RECONFIG_RES: {
uint16_t result;
STREAM_TO_UINT16(result, p); // 【1】漏洞点
......